Web Security Academy – Reflected XSS with some SVG markup allowed – Swimming in the Byte Stream
Por um escritor misterioso
Descrição
We need to capture a simple search from the homepage and send it to the Burp Suite Intruder the Repeater. Remove the default wildcards from the Intruder and add them to the search field like so: No…

Critical Adobe Flaws Allow Attackers to Run JavaScript in Br

ELearnSecurity EWPT Notes, PDF, Http Cookie

PDF) RESOURCE RELIABILITY AND INTEGRITY ASSURANCE WITH BLOCKCHAIN

Swimming in the Byte Stream – My Infosec Journey

CUBA Platform. Developer's Manual

Reflected XSS with some SVG markup allowedをやってみた - Shikata

PortSwigger Labs - Reflected XSS with some SVG markup allowed
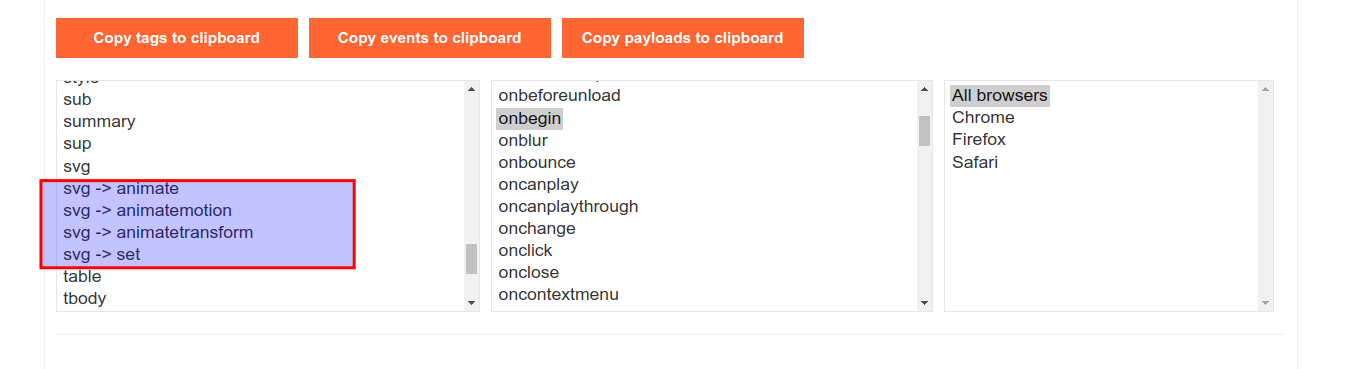
Reflected XSS with Some SVG Markup, by İbrahim Taha İstikbal

Ultimate Guide to Coding PSD to HTML from Front-end Experts

Our blog - Seahawk

Computer Systems Security: Planning for Success
Supply Chain Security Begins with Secure Software Development
de
por adulto (o preço varia de acordo com o tamanho do grupo)