How ransomware attackers evade your organization's security
Por um escritor misterioso
Descrição
How ransomware operators avoid your security solutions and what you can do to protect your network against post-compromise ransomware attacks.
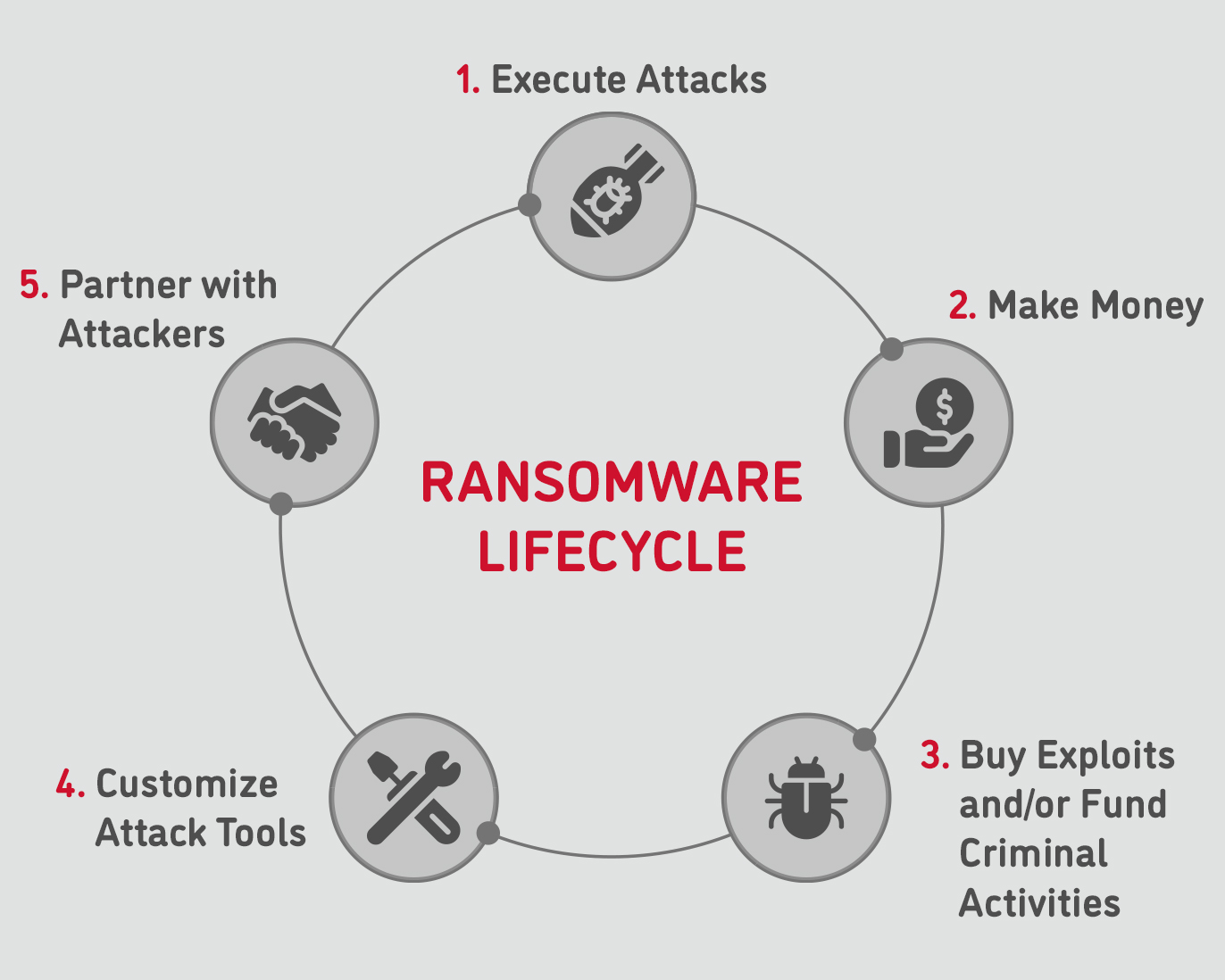
Ransomware Attack - Prevention, Detection, Simulation

What are Indicators of Compromise (IoCs)? A Comprehensive Guide - SentinelOne
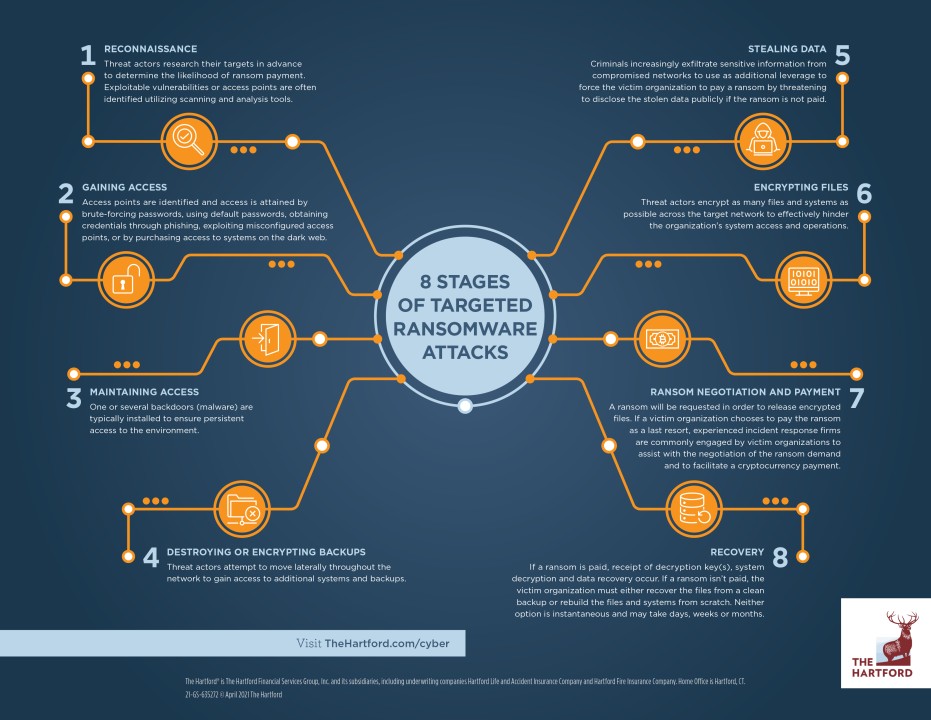
Anatomy of a Ransomware Attack: a Guide to Prevention and Recovery

RH-ISAC, Preventing Ransomware Attacks in a Hybrid Cloud

Ransomware in Public Clouds: How TTPs Could Change

7 Tips to Prepare Against Ransomware, Expert View

Ransomware Attack Vectors and How to Avoid Them

How to Prevent Ransomware Attacks: Top 10 Best Practices in 2023

What's New in Ransomware & How to Avoid an Attack - The Wursta Corporation

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA
de
por adulto (o preço varia de acordo com o tamanho do grupo)
_new-roblox-evade-script-hack-gui-124-auto-farm-124-god-mode-124-infinite-money-amp-more-pastebin-2022-preview-hqdefault.jpg)




