DoorDash Supply-Chain Attack - Secplicity - Security Simplified
Por um escritor misterioso
Descrição
DoorDash is a popular food delivery service – and very convenient if I say so myself. However, in the seemingly never-ending trend of cyber attacks, DoorDash, too, fell victim to a supply-chain attack. Earlier this month, DoorDash identified unusual activity via a third-party service. They immediately launched an investigation and have consulted with outside agencies. […]

Prevent a Supply Chain Attack on Your CI/CD Server JetBrains: Developer Tools for Professionals and Teams

Brand New: New Logo and Identity for Airbnb by DesignStudio
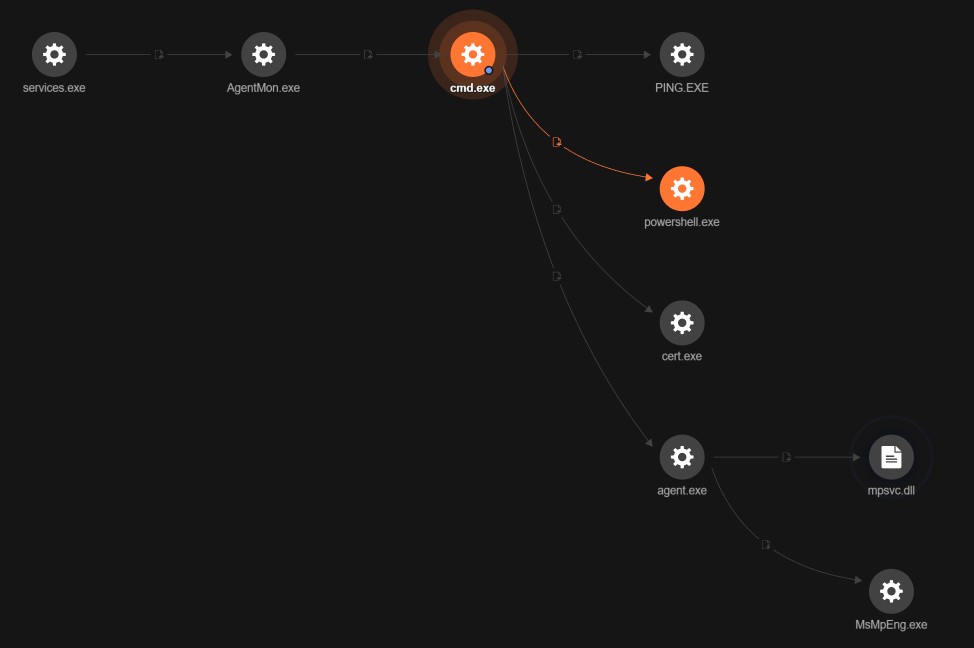
Supply Chain Attacks from a Managed Detection and Response Perspective

My DoorDash Redesign: Introducing GateDash, food delivery at the airport!, by Xinyi Xu

Supply Chain Attacks and Critical Infrastructure: How CISA Helps Secure a Nation's Crown Jewels

Supply Chain Attack Examples And Prevention Measures

Hacking the Supply Chain Air & Space Forces Magazine
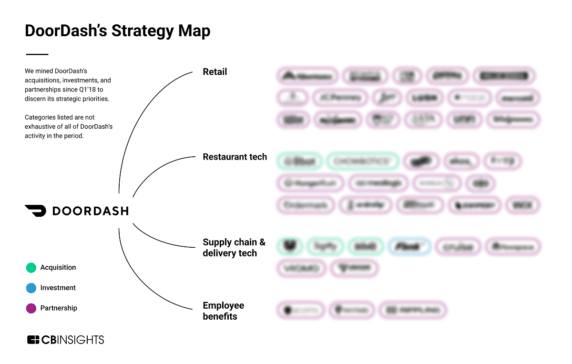
Analyzing DoorDash's operational strategy: How the delivery leader is investing in local commerce - CB Insights Research

Airbnb logo, Airbnb, Identity logo
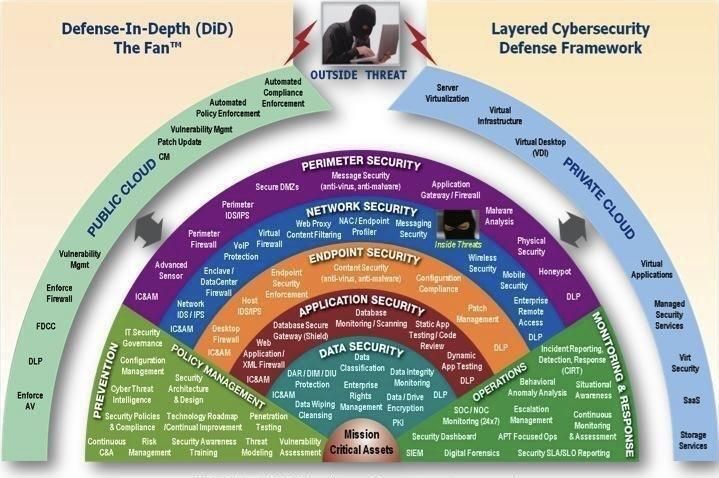
How Do You Protect Against Supply Chain Attacks?

Software supply chain attacks: why every link matters – Sysdig
Supply chain attack: What it is and how does it work?
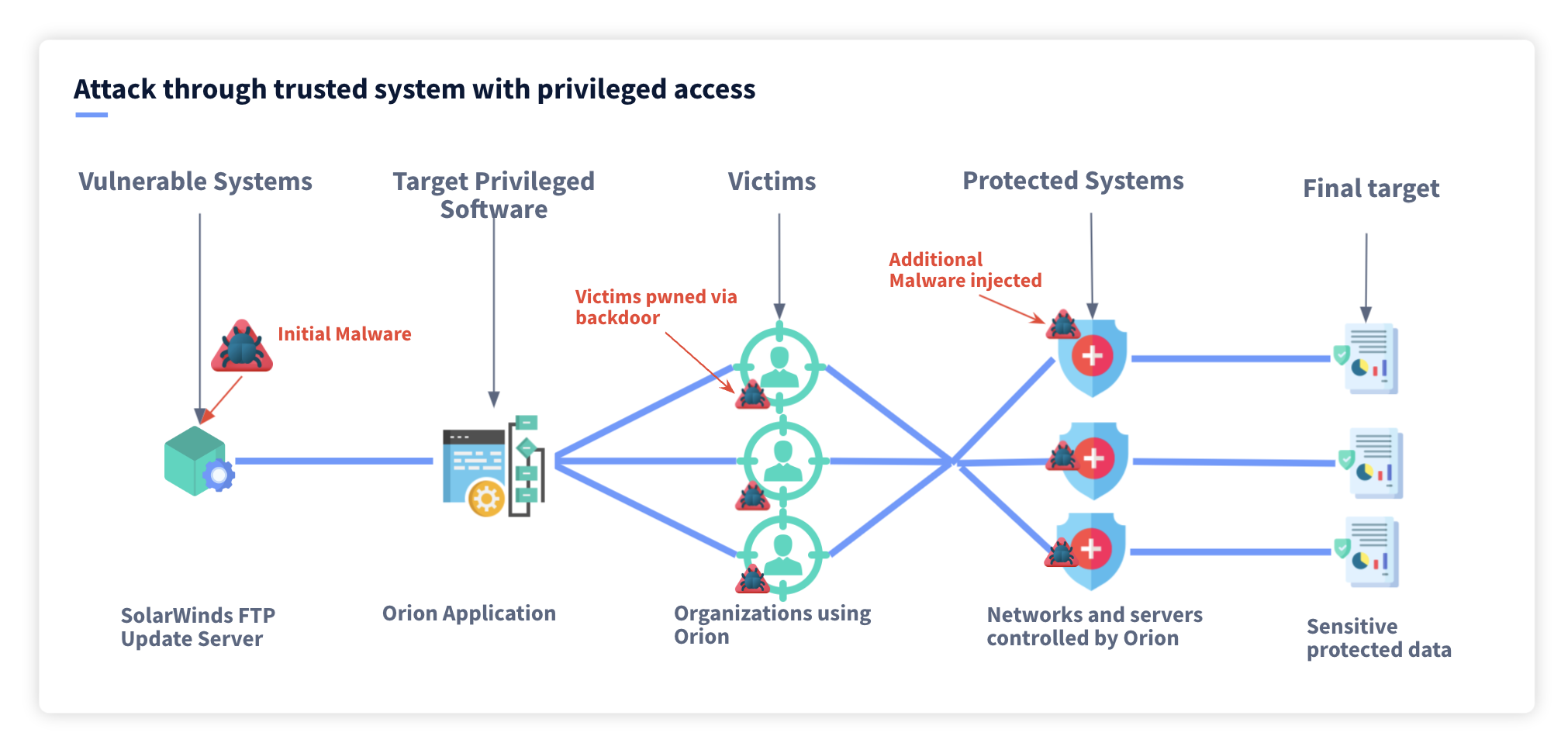
Supply Chain Attacks: 6 Steps to protect your software supply chain

Using Microsoft 365 Defender to protect against Solorigate
How we'll solve software supply chain security
de
por adulto (o preço varia de acordo com o tamanho do grupo)