Solved How could an adversary obtain remote screen access to
Por um escritor misterioso
Descrição
Answer to Solved How could an adversary obtain remote screen access to

Explain Like I'm 5: Remote Desktop Protocol (RDP)

MFA Fatigue: Hackers' new favorite tactic in high-profile breaches

Taking Over the Overlay: Reverse Engineering a Brazilian Remote Access Trojan (RAT)
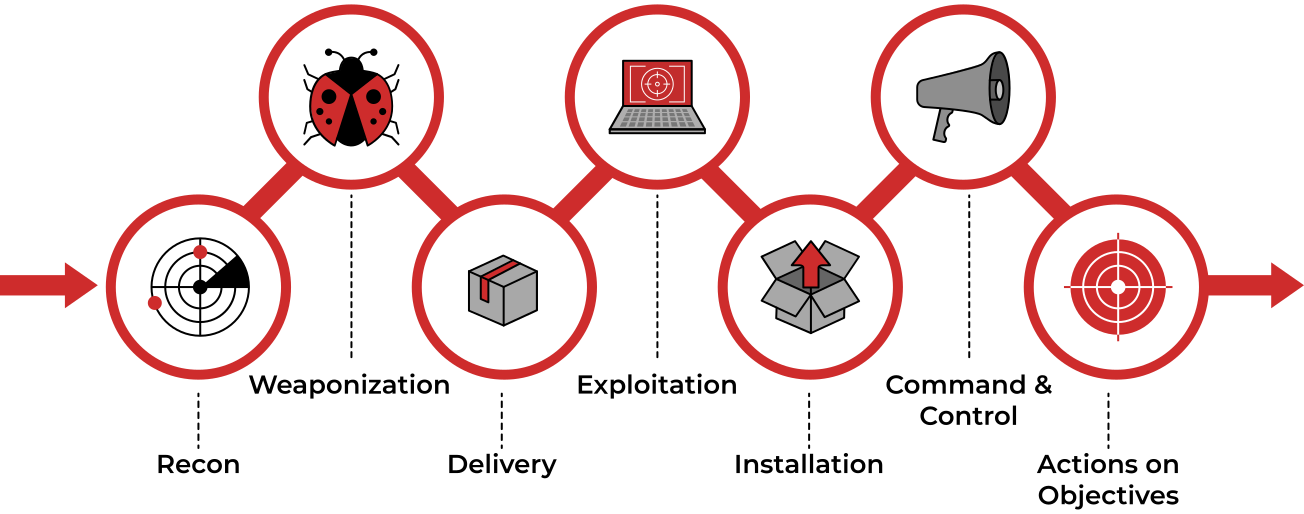
TryHackMe Cyber Kill Chain Room. The Cyber Kill Chain framework is…, by Haircutfish

RDP Hacking: How Hackers Enter Remote Desktops & How to Be Safe

Remote Hackers and Remote Attacks

Attacking RDP from Inside: How we abused named pipes for smart-card hijacking, unauthorized file sys

The risks of remote desktop security & how to overcome them

RDP Access: 8 Ways to Protect Against Remote Vulnerabilities
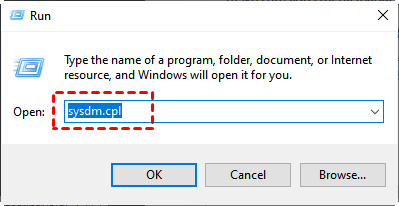
RDP Vulnerabilities and How to Avoid RDP Exploits
de
por adulto (o preço varia de acordo com o tamanho do grupo)