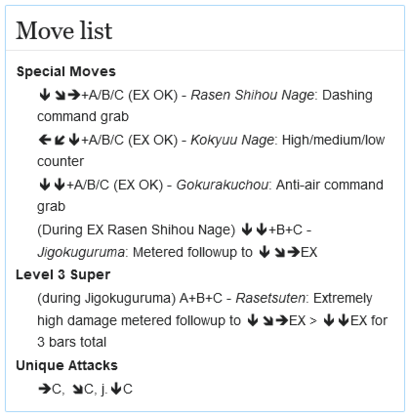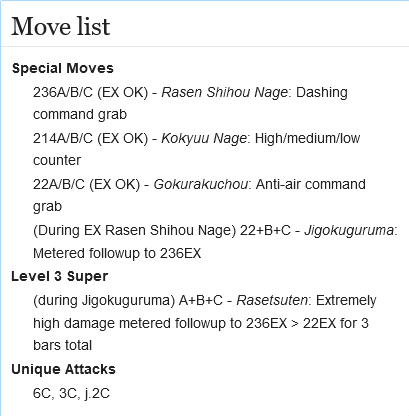
The Evolution of ShellBot Malware: A Dive into Hexadecimal Notation
Por um escritor misterioso
Descrição
Threat actors are constantly innovating to stay one step ahead. One such innovation is the use of hexadecimal notation in the distribution of ShellBot malware. AhnLab Security Emergency Response Center (ASEC) recently reported a shift in the tactics employed by cybercriminals to distribute ShellBot, a DDoS malware targeting Linux SSH
Threat actors are constantly innovating to stay one step ahead. One such innovation is the use of hexadecimal notation in the distribution of ShellBot malware. AhnLab Security Emergency Response Center (ASEC) recently reported a shift in the tactics employed by cybercriminals to distribute ShellBot, a DDoS malware targeting Linux SSH servers. Let's delve into the nitty-gritty of this development, shall we? The Old Ways: Dot-Decimal Notation Traditionally, ShellBot was distributed using IP addr
Threat actors are constantly innovating to stay one step ahead. One such innovation is the use of hexadecimal notation in the distribution of ShellBot malware. AhnLab Security Emergency Response Center (ASEC) recently reported a shift in the tactics employed by cybercriminals to distribute ShellBot, a DDoS malware targeting Linux SSH servers. Let's delve into the nitty-gritty of this development, shall we? The Old Ways: Dot-Decimal Notation Traditionally, ShellBot was distributed using IP addr

IT threat evolution Q2 2020. PC statistics - vulnerability database
ARANET LLC.: [New post] Microsoft Exposes Russian Hackers' Sneaky Phishing Tactics via Microsoft Teams Chats

K9s: How to manage your Kubernetes clusters in style!, Saeid Saebi posted on the topic

Analysis Report on Lazarus Threat Group's Volgmer and Scout Malware - ASEC BLOG
RST TI Report Digest: 16 Oct 2023, by RST Cloud, Oct, 2023

QakBot Malware Group Increases Command and Control Network with Additional 15 New Servers
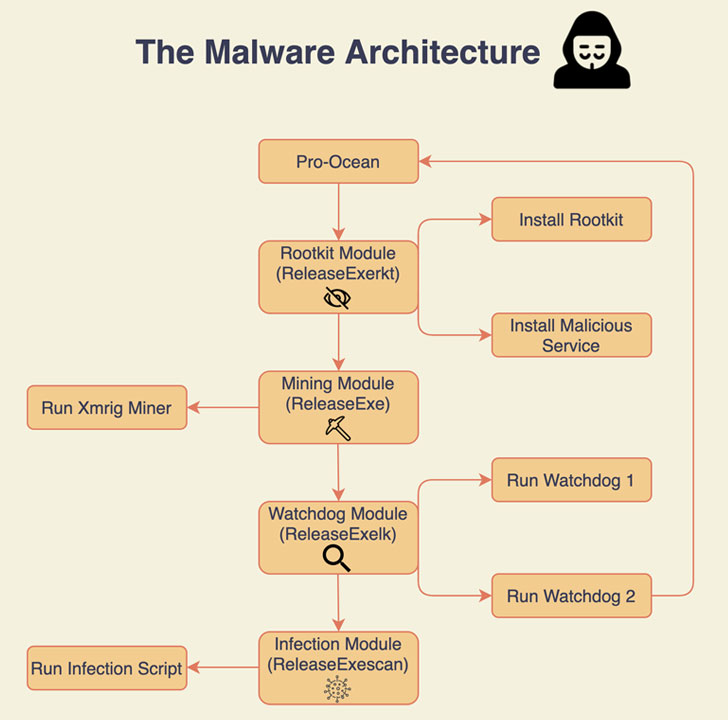
New Cryptojacking Malware Targeting Apache, Oracle, Redis Se - vulnerability database

ShellBot Uses Hex IPs to Evade Detection in Attacks on Linux SSH Servers

PDF) A Near Real-Time Scheme for Collecting and Analyzing IoT Malware Artifacts at Scale

Analysis Report on Lazarus Threat Group's Volgmer and Scout Malware - ASEC BLOG
de
por adulto (o preço varia de acordo com o tamanho do grupo)