CS 5430 System Security -- Chinese Wall Policies
Por um escritor misterioso
Descrição

Figure 1 from A practical Chinese wall security model in cloud computing

exh10ormofunitfranchised

ANHUI PROVINCE FAMILY DIRECTORY: A list of families who have

Novel Paraquat Detection Strategy Enabled by Carboxylatopillar[5]arene Confined in Nanochannels on a Paper-Based Sensor

NIST SP 800-82r3 Ipd, PDF, Security

Least-restrictive enforcement of the Chinese wall security policy Proceedings of the 18th ACM symposium on Access control models and technologies

CHinese Wall Security Policy

Security Policies and Security Models by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu
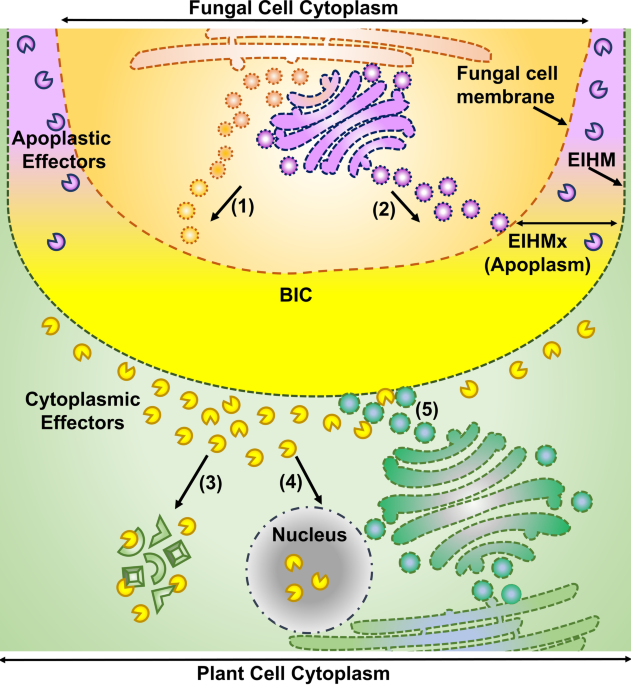
Arms and ammunitions: effectors at the interface of rice and it's pathogens and pests, Rice

POSTER ABSTRACTS - 2023 - Haemophilia - Wiley Online Library

VILLANOVA UNIVERSITY CATALOG

Figure 4 from A new Access Control model based on the Chinese Wall Security Policy Model
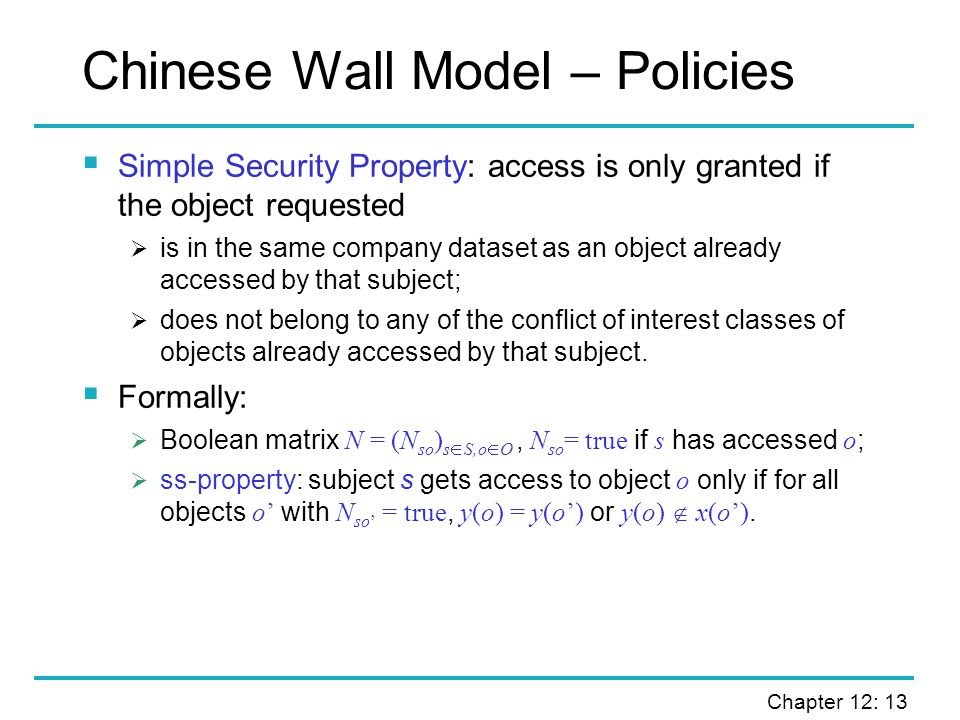
Computer Security 3e Dieter Gollmann - ppt video online download

1 TOPIC THE CHINESE WALL LATTICE Ravi Sandhu. 2 CHINESE WALL POLICY Example of a commercial security policy for confidentiality Mixture of free choice. - ppt download
de
por adulto (o preço varia de acordo com o tamanho do grupo)







