Operation Exchange Marauder: Active Exploitation of Multiple Zero-Day Microsoft Exchange Vulnerabilities
Por um escritor misterioso
Descrição
[UPDATE] March 8, 2021 – Since original publication of this blog, Volexity has now observed that cyber espionage operations using the SSRF vulnerability CVE-2021-26855 started occurring on January 3, 2021, three days earlier than initially posted. Volexity is seeing active in-the-wild exploitation of multiple Microsoft Exchange vulnerabilities used to steal e-mail and compromise networks. These attacks appear to have started as early as January 6, 2021. In January 2021, through its Network Security Monitoring service, Volexity detected anomalous activity from two of its customers' Microsoft Exchange servers. Volexity identified a large amount of data being sent to IP addresses it believed were not tied to legitimate users. A closer inspection of the IIS logs from the Exchange servers revealed rather alarming results. The logs showed inbound POST requests to valid files associated with images, JavaScript, cascading style sheets, and fonts used by Outlook Web Access (OWA). It was initially suspected the […]
Examining Exchange Exploitation and its Lessons for Defenders - DomainTools
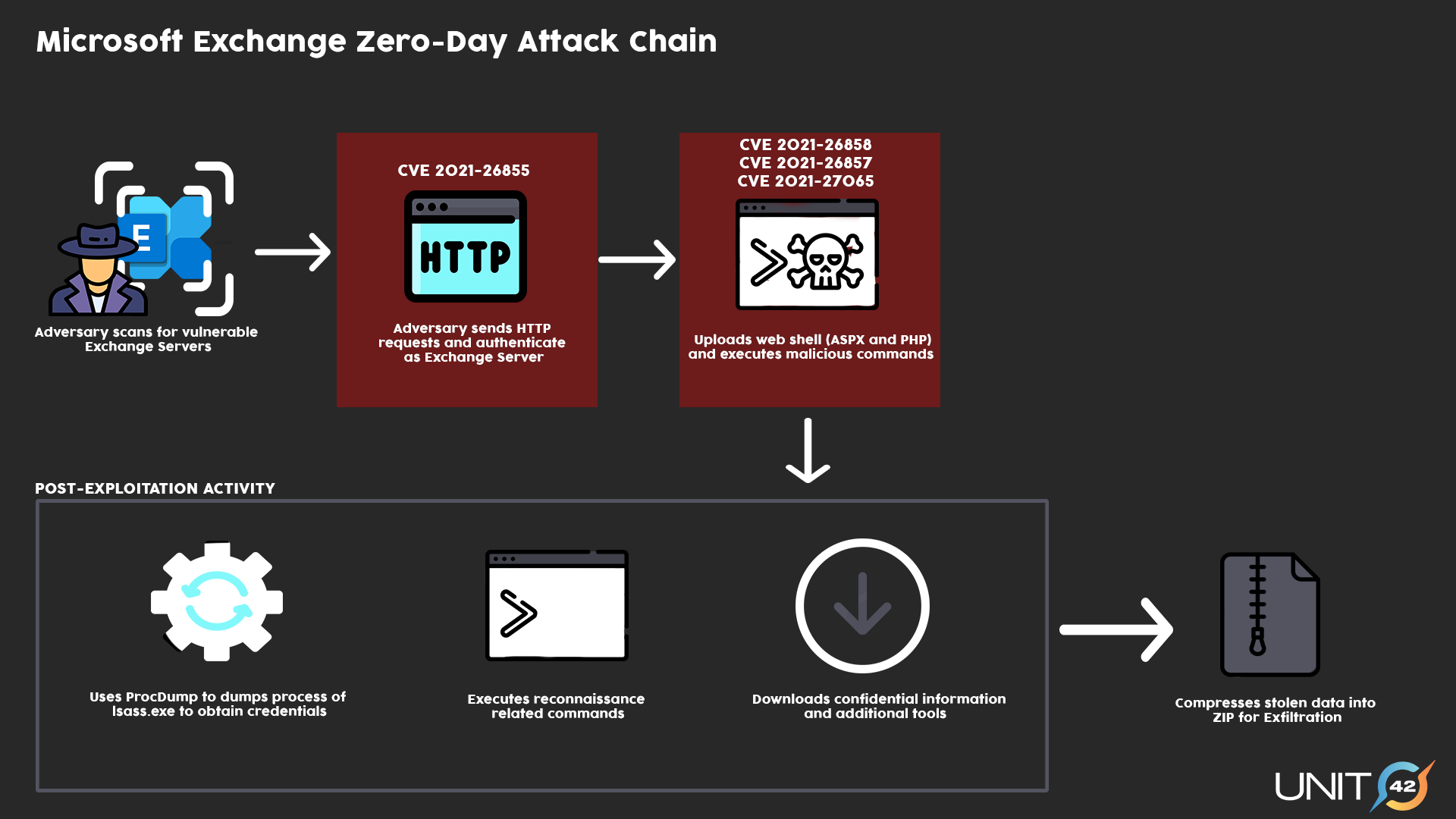
Threat Assessment: Active Exploitation of Four Zero-Day Vulnerabilities in Microsoft Exchange Server

Attackers Exploit New Zero-Day ProxyNotShell Vulnerabilities on Exchange Server

ProxyNotShell: A Zero-Day Microsoft Exchange Exploit

Examining Exchange Exploitation and its Lessons for Defenders - DomainTools

Tactics, Techniques, and Procedures (TTPs) Used by HAFNIUM to Target Microsoft Exchange Servers
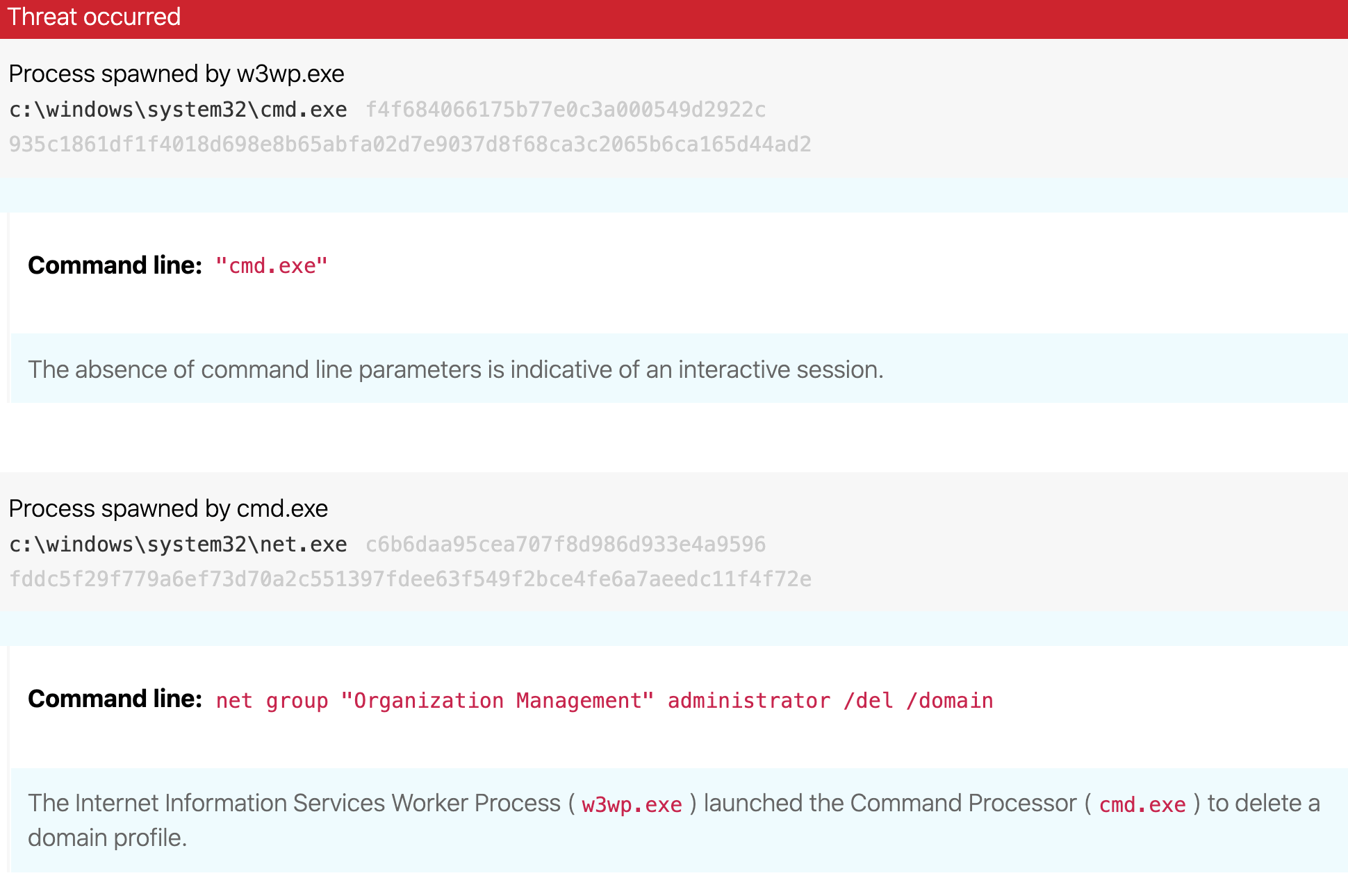
Microsoft Exchange exploitation: how to detect, mitigate, and stay calm

Microsoft Exchange Server Zero-Day Vulnerabilities Exploited

Finding Proxylogon and Related Microsoft Exchange Vulnerabilities: How Tenable Can Help - Blog
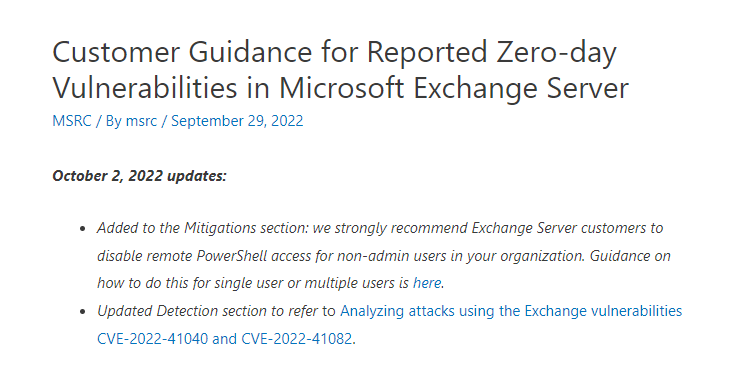
Exploitation of Microsoft Exchange Servers seen in the wild – PwnDefend

Operation Exchange Marauder - SOC Prime

Network Break 323: Google To Swap 3rd-Party Cookies For Cohorts; Attackers Exploit On-Prem Exchange - Packet Pushers
de
por adulto (o preço varia de acordo com o tamanho do grupo)