Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Detail procedure of malware analysis

Intro to Malware Analysis: What It Is & How It Works - InfoSec
Malware analysis

Routers Roasting on an Open Firewall: the KV-botnet Investigation
Malware analysis

Mastering Malware Analysis
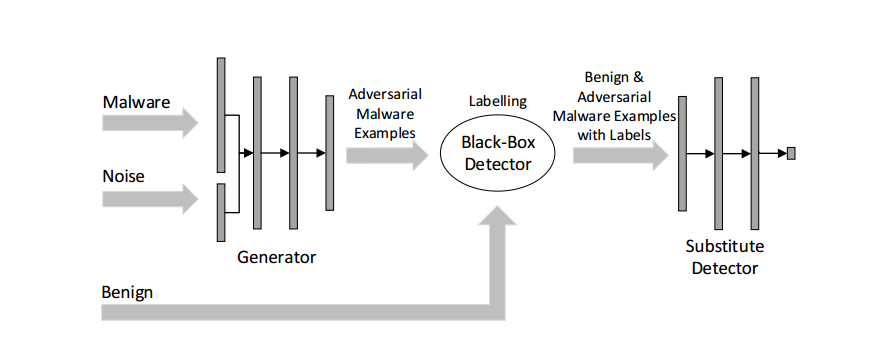
Malware Detection

Top 10 Types of Information Security Threats for IT Teams

Brute Force Attacks: Password Protection

TryHackMe Hacktivities

Malware analysis metasploit.bat Malicious activity
de
por adulto (o preço varia de acordo com o tamanho do grupo)