Grouping Multiparty Key Generation.
Por um escritor misterioso
Descrição

How to secure digital assets with multi-party computation and Confidential Space
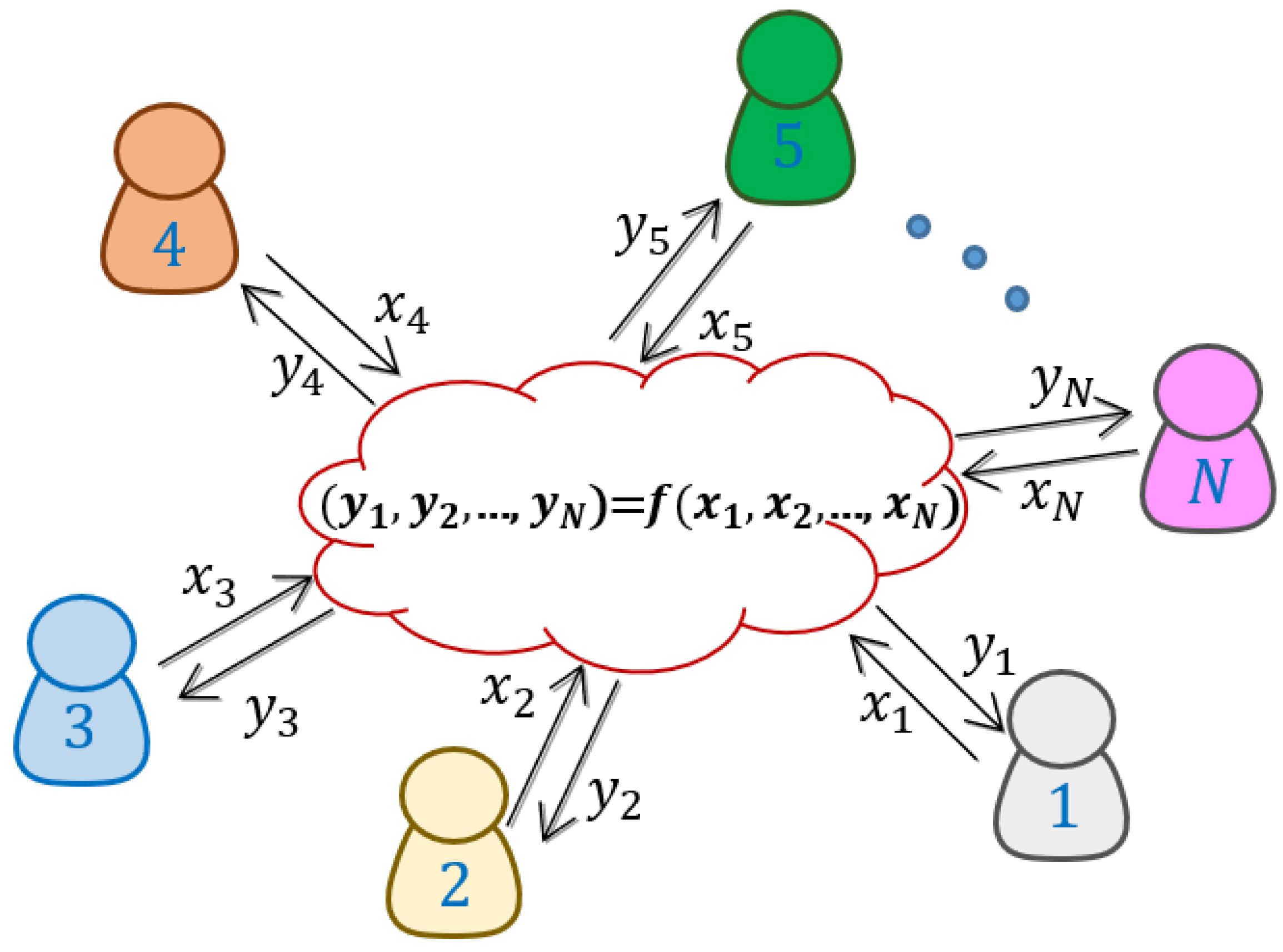
Applied Sciences, Free Full-Text
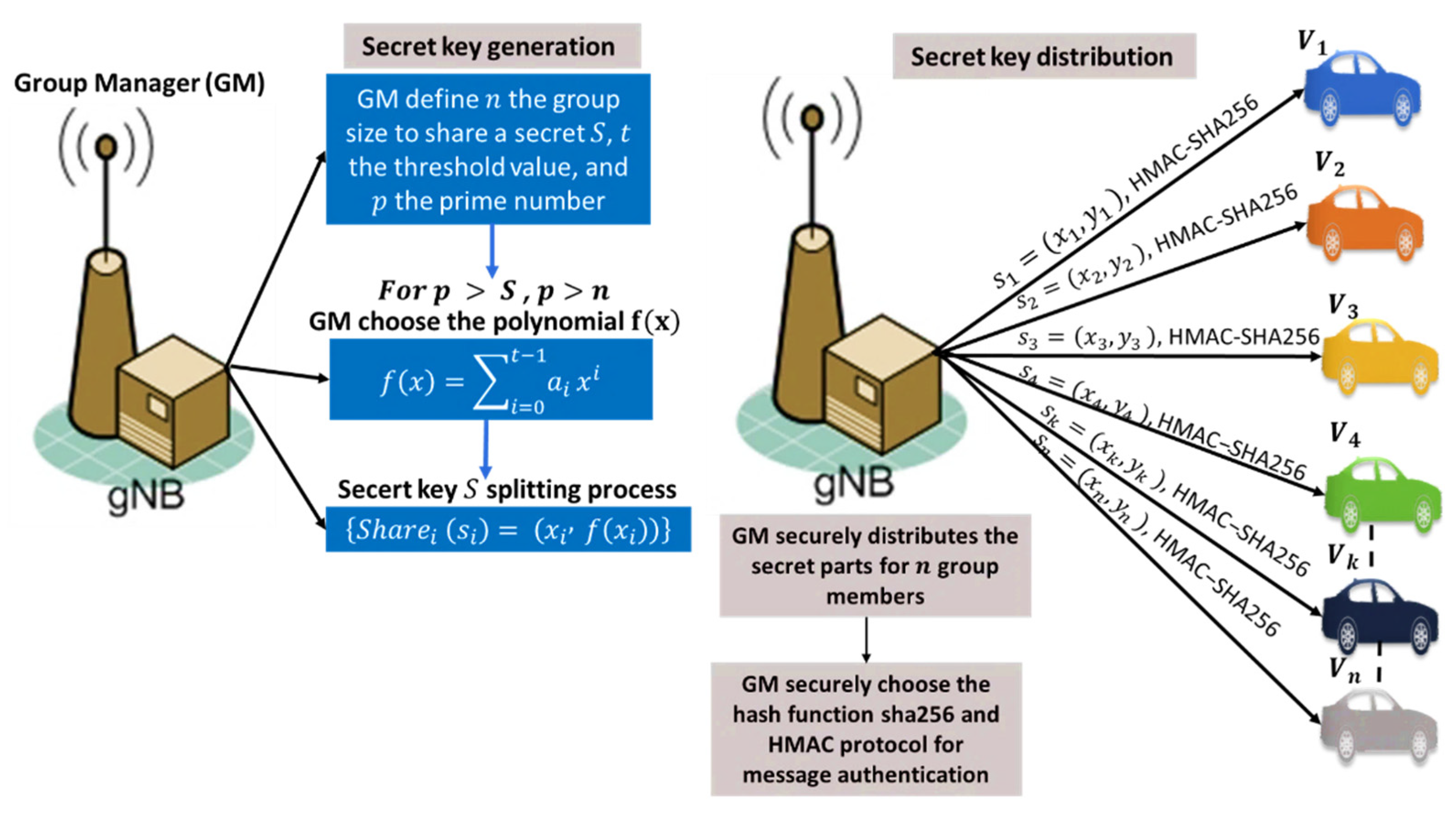
Sensors, Free Full-Text

MetaMask Institutional Onboards Four New Institutional Custodians, Consolidating its Leadership as the Go-to Solution for Organizations Entering Web3
Secure Multi-Party Computation (MPC): A Deep Dive

Efficient sharing of privacy-preserving sensing data on consortium blockchain via group key agreement - ScienceDirect

PDF] Efficient RSA Key Generation Protocol in a Two-Party Setting and its Application into the Secure Multiparty Computation Environment
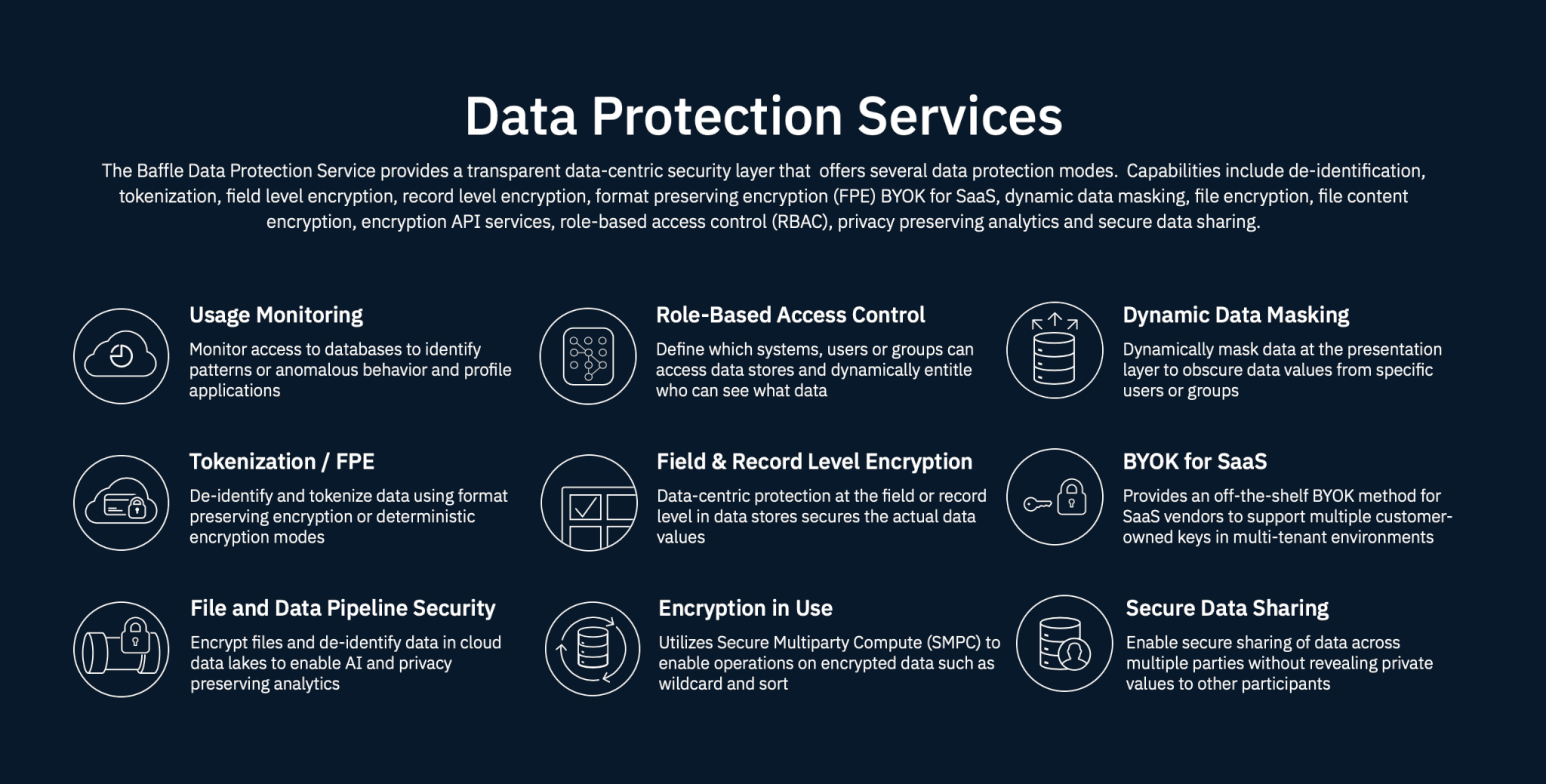
Database Encryption, De-Identification, Data Masking, More

TrustGWAS: A full-process workflow for encrypted GWAS using multi-key homomorphic encryption and pseudorandom number perturbation - ScienceDirect

What Is the Threshold Signature Scheme?
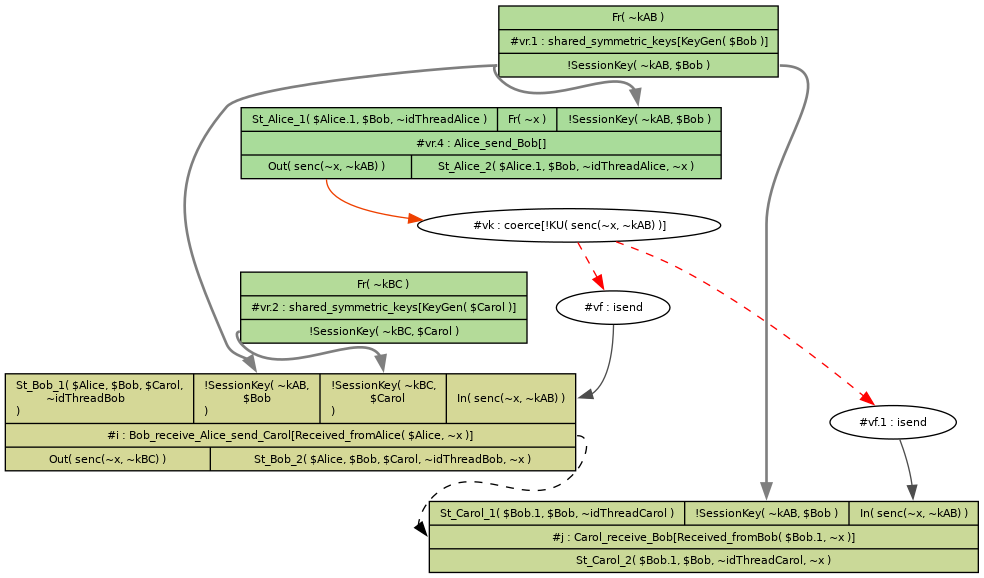
Modelling multiparty protocols

Multi-party interactive cryptographic key distribution protocol over a public network based on computational ghost imaging - ScienceDirect
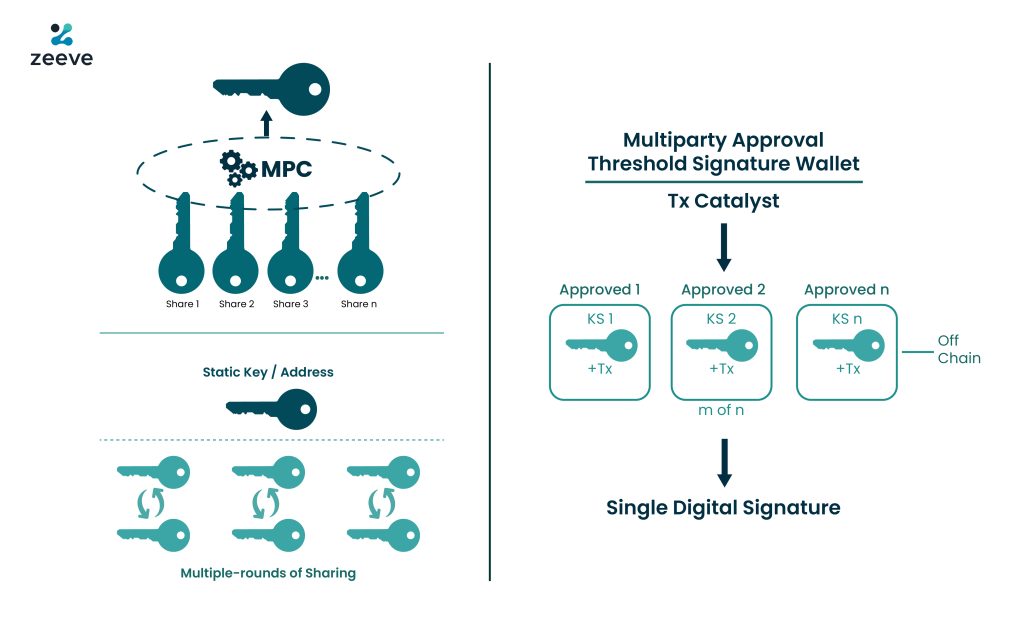
What is the Threshold signature scheme(TSS)? Multi-party Computation(MPC) simplified
de
por adulto (o preço varia de acordo com o tamanho do grupo)