Reverse engineering Emotet – Our approach to protect GRNET against the trojan
Por um escritor misterioso
Descrição
Emotet Uses Camouflaged Malicious Macros to Avoid Antivirus Detection
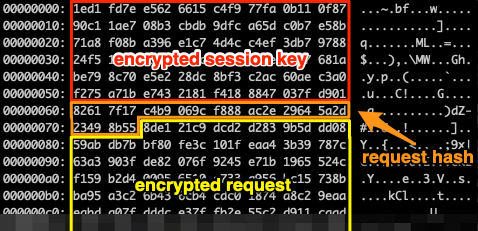
Reverse engineering Emotet – Our approach to protect GRNET against the trojan

A full reverse engineering analysis of the emotet trojan : r/ ReverseEngineering
Methodology for Reverse-Engineering Malware

A full reverse engineering analysis of the emotet trojan : r/netsec

A full reverse engineering analysis of the emotet trojan : r/netsec

Dimitris Kolotouros (@kolotoor) / X

What is Emotet? And how to guard against this persistent Trojan malware

Fig. no 7: Best approaches to prevent Emotet Malware or any other
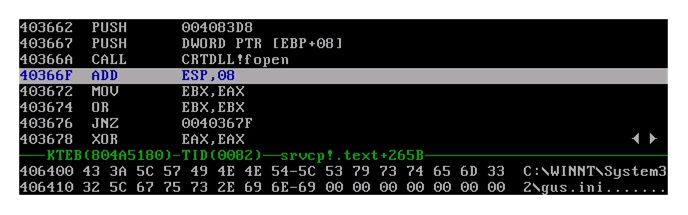
Methodology for Reverse-Engineering Malware
Emotet Malware 0x01 - MalGamy
Trojan.Emotet
Methodology for Reverse-Engineering Malware
Emotet Malware: Wild, Wild Trojan Malware
de
por adulto (o preço varia de acordo com o tamanho do grupo)